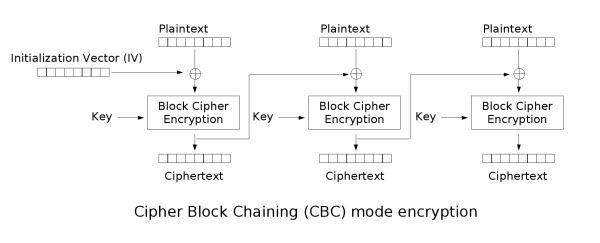
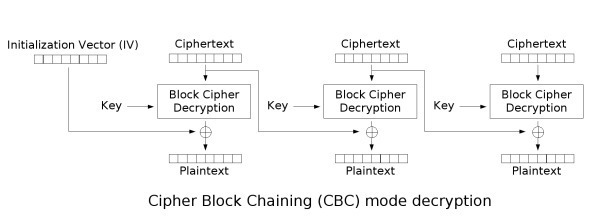
Bit-flipping attack
########################################################################
# Welcome to the Bank of the World #
# All connections are monitored and recorded #
# Disconnect IMMEDIATELY if you are not an authorized user! #
########################################################################
...sending None...
Leaked ciphertext: 2df81f67375997277269a2cbfcca0be242bca2d674165b70cbd21ac7feb8385e4c4e64066f6a1c9be9801bec05689621
enter ciphertext:
...sending b'2df81f67375997277269a2cbfcca0be242bca2d674165b70cbd21ac7feb8385e4c4e64066f6a1c9be9801bec05689621'...
Please try again.
...sending None...
...sending None...
username:
...sending b'bdmin'...
bdmin's password:
...sending b'g0ld3n_b0y'...
########################################################################
# Welcome to the Bank of the World #
# All connections are monitored and recorded #
# Disconnect IMMEDIATELY if you are not an authorized user! #
########################################################################
...sending None...
Leaked ciphertext: 2df81f67375997277269a2cbfcca0be242bca2d674165b70cbd21ac7feb8385e4c4e64066f6a1c9be9801bec05689621
enter ciphertext:
...sending b'2ef81f67375997277269a2cbfcca0be242bca2d674165b70cbd21ac7feb8385e4c4e64066f6a1c9be9801bec05689621'...
Logged in successfully!
Your flag is: HTB{b1t_fl1pp1ng_1s_c00l}
#app.py
import socketserver
import socket, os
from Crypto.Cipher import AES
from Crypto.Util.Padding import pad,unpad
from Crypto.Random import get_random_bytes
from binascii import unhexlify
from secret import FLAG
wlcm_msg ='########################################################################\n'+\
'# Welcome to the Bank of the World #\n'+\
'# All connections are monitored and recorded #\n'+\
'# Disconnect IMMEDIATELY if you are not an authorized user! #\n'+\
'########################################################################\n'
key = get_random_bytes(16)
iv = get_random_bytes(16)
def encrypt_data(data):
padded = pad(data.encode(),16,style='pkcs7')
cipher = AES.new(key, AES.MODE_CBC,iv)
enc = cipher.encrypt(padded)
return enc.hex()
def decrypt_data(encryptedParams):
cipher = AES.new(key, AES.MODE_CBC,iv)
paddedParams = cipher.decrypt( unhexlify(encryptedParams))
print(paddedParams)
if b'admin&password=g0ld3n_b0y' in unpad(paddedParams,16,style='pkcs7'):
return 1
else:
return 0
def send_msg(s, msg):
enc = msg.encode()
s.send(enc)
def main(s):
send_msg(s, 'username: ')
user = s.recv(4096).decode().strip()
send_msg(s, user +"'s password: " )
passwd = s.recv(4096).decode().strip()
send_msg(s, wlcm_msg)
msg = 'logged_username=' + user +'&password=' + passwd
try:
assert('admin&password=g0ld3n_b0y' not in msg)
except AssertionError:
send_msg(s, 'You cannot login as an admin from an external IP.\nYour activity has been logged. Goodbye!\n')
raise
msg = 'logged_username=' + user +'&password=' + passwd
send_msg(s, "Leaked ciphertext: " + encrypt_data(msg)+'\n')
send_msg(s,"enter ciphertext: ")
enc_msg = s.recv(4096).decode().strip()
try:
check = decrypt_data(enc_msg)
except Exception as e:
send_msg(s, str(e) + '\n')
s.close()
if check:
send_msg(s, 'Logged in successfully!\nYour flag is: '+ FLAG)
s.close()
else:
send_msg(s, 'Please try again.')
s.close()
class TaskHandler(socketserver.BaseRequestHandler):
def handle(self):
main(self.request)
if __name__ == '__main__':
socketserver.ThreadingTCPServer.allow_reuse_address = True
server = socketserver.ThreadingTCPServer(('0.0.0.0', 1337), TaskHandler)
server.serve_forever()#flipper
import socket, os
import re
from binascii import unhexlify
def send_request(socket, data):
print(f'...sending {data}...')
if data is not None:
socket.sendall(data)
data = socket.recv(8092).decode().strip()
return data
def extract_cipher(data):
match = re.search(r'Leaked ciphertext:\s(.*)', data)
return unhexlify(match[1])
def flip_bit(data, i):
return (i).to_bytes(1, byteorder="big") + data[1:48]
if __name__ == "__main__":
HOST = '46.101.12.68'
PORT = 30068
# HOST = '127.0.0.1'
# PORT = 1337
for i in range(0, 255):
with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s:
s.connect((HOST, PORT))
data = None
# initial request
data = send_request(s, None)
#print(data)
# submit username
data = send_request(s, b'bdmin')
# print(data)
# submit password
data = send_request(s, b'g0ld3n_b0y') # e must be replaced with 3 through bit flipping
# print(data)
data = send_request(s, None)
# print(data)
# extract cipher
cipher = extract_cipher(data)
# flip a bit
flipped_cipher = flip_bit(cipher, i)
data = send_request(s, flipped_cipher.hex().encode())
print(data)
if re.search(r'successfully', data):
quit()
# final request
data = send_request(s, None)
print(data) #fake_enc[15] = fake_enc[15] ^ ord('m') ^ ord('n')
#username=12345678901admim,password=g0ld3n_b0y
from Crypto.Cipher import AES
from Crypto.Util.Padding import pad,unpad
from Crypto.Random import get_random_bytes
from binascii import unhexlify
m = 'logged_username=12345678901admim&password=g0ld3n_b0y'
key = get_random_bytes(16)
iv = get_random_bytes(16)
def encrypt_data(data):
padded = pad(data.encode(),16,style='pkcs7')
cipher = AES.new(key, AES.MODE_CBC,iv)
enc = cipher.encrypt(padded)
return enc.hex()
def decrypt_data(encryptedParams):
cipher = AES.new(key, AES.MODE_CBC,iv)
paddedParams = cipher.decrypt( unhexlify(encryptedParams))
print(paddedParams)
if b'admin&password=g0ld3n_b0y' in unpad(paddedParams,16,style='pkcs7'):
return 1
else:
return 0
#enc = encrypt_data(m)
enc = '3df84215ed6f9ed37eaef8025dbbe28edaca4e9a9f0f8bd4334cc1aff4c217e2694f5bb38b137b2cde2d5051f63466ef29930ec3d34d805bf466daffadafc98f'
fake_enc = bytes.fromhex(enc)
fake_enc = list(fake_enc)
fake_enc[15] = fake_enc[15] ^ ord('m') ^ ord('n')
fake_enc = bytes(fake_enc).hex()
print(fake_enc)
dec = decrypt_data(fake_enc) # enc
print(dec)